German Telekom Bug Bounty Program - Scope changes! Exclude of 3 Bug Types
The official Telekom Bug Bounty Program announced since december 2013 that in 2014 the vulnerability scope guidlines became a persistent upgrade.
A lot of unauthorized individuals have submitted a lot of client-side cross site scripting vulnerabilities by usage of public security scanners software/scripts.
The reports overflowed the telekom program and as consequence a major update to change came up by exclude of several "small" attacks vectors.
They do not block to receive client-side cross site issues because they also need to patch them but the main scope has been changed to major security issues in 2014.
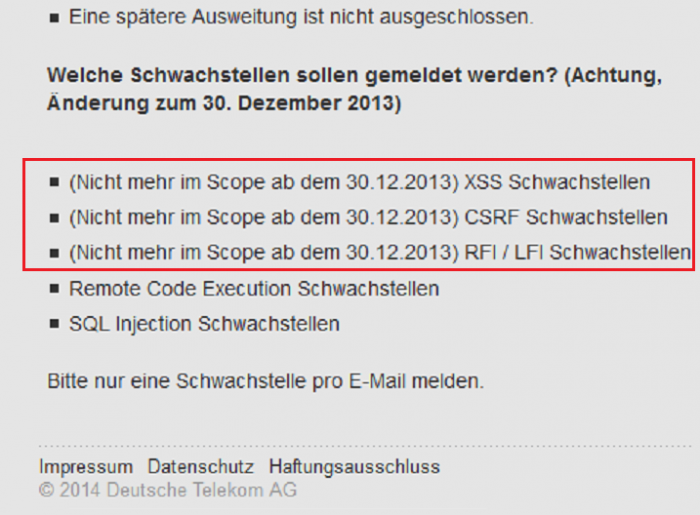
The german telekom decided to disallow to reward the following categories of bugs:
(Out of Scope - begin 30.12.2013) - Cross Site Scripting Vulnerabilities
(Out of Scope - begin 30.12.2013) - Cross Site Request Forgery Issues
(Out of Scope - begin 30.12.2013) - Remote File Include Vulnerabilities & Local File Include Vulnerabilities
Earlier send vulnerability reports will be acknowledged by the telekom. The researcher will receive the regular bug bounty payment by the german telekom after the patch has been discovered. Still in scope of the program are the following categories of bugs:
(Scope) Remote & Local Code Execution Vulnerabilities
(Scope) SQL Injection Vulnerabilities & DBMS Injection Bugs
(Scope) Auth Bypass, Filter Bypass or Token Bypass Vulnerabilities
(Scope) Crypto Weakness or Vulnerabilities
The telekom security team added also the following sentence "A later extension is not excluded". Means the program can expand for researchers, analysts or other individuals in 2014 after successful participation.
Reference(s): http://www.telekom.com/bug-bounty



Add new comment