Paypal Inc - Medium Severity Open Redirect Web Vulnerability fixed!
Paypal Inc - Medium Severity Open Redirect Web Vulnerability fixed!
Security researcher Ayoub Ait Elmokhtar found an Open Redirect Web Vulnerability (EIBBP-32252) in the official PayPal web application. The vulnerability has been accepted by Paypal and the researcher was rewarded with 250 US$. The researcher started the research by the use of different versions of known redirect issues like for instance:
https://www.google.com/search?btnI&q=allinurl:evolution-sec.com
It will redirect you to evolution-sec.com since this is an open redirect vulnerability in Google, since Google allow open redirect and didn't consider it in scope of Bug Bounty.
So appending this link url and visiting : email-edg.paypal.com/r/VTHX7UY/LP46GM/2OE8AOD/D9NJX6/74IKNJ/2V/h?a=https://www.google.com/search?btnI&q=allinurl:evolution-sec.com
It seems like it will redirect to evolution-sec.com but it won't - it will endup with a result which clearly appear to be a filter against directory filtering. This assumes that everything after www.domaine.com in this parameter won't work. Well if we try accessing a subdomaine of google like http://XXX.google.com it will not work and no redirection takes place.
So this is clearly appear to be some Oauth rules about redirect parameter rules:
1 - Subdomaine Filter
2 - Directory Filter
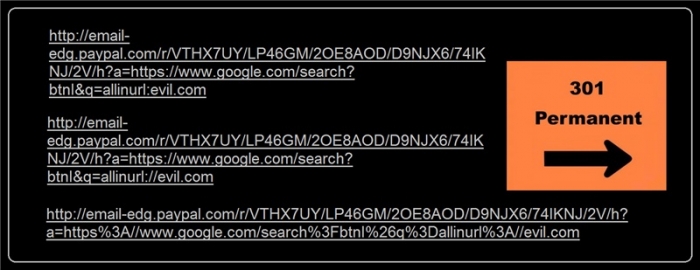
The final working POC which bypass the directory filtering :
So this worked: email-edg.paypal.com/r/VTHX7UY/LP46GM/2OE8AOD/D9NJX6/74IKNJ/2V/h?a=https://www.google.com/search?btnI&q=allinurl://evil.com
This worked not: email-edg.paypal.com/r/VTHX7UY/LP46GM/2OE8AOD/D9NJX6/74IKNJ/2V/h?a=https://www.google.com/search?btnI&q=allinurl:evil.com
You should see the bypass with // which is likely an old python library URL rules bypass.
Oauth documentation say that you shouldn't accept subdomaines neither directories in the redirect url.
FINAL POC (does not work anylonger because the vulnerability has been patched by PayPal.
email-edg.paypal.com/r/VTHX7UY/LP46GM/2OE8AOD/D9NJX6/74IKNJ/2V/h?a=https%3A//www.google.com/search%3FbtnI%26q%3Dallinurl%3A//evil.com
References



Comments
Congratulations
Nice finding man , you catch it (y) keep it up.
Super!
Nice bro!
Add new comment