Facebook Bug Bounty - Restriction Filter Bypass Vulnerability (ID 221374210)
Facebook Bug Bounty - Restriction Filter Bypass Vulnerability
Today the vulnerability researcher "Paulos Yibelo" (18) discovered a restriction filter bypass vulnerability in the facebook social network web-application. The vulnerability had medium severity. The facebook developer team patched the issue to the new year by coordination of the facebook whitehat security team. The issue was official send as report to the official facebook whitehat bug bounty program.
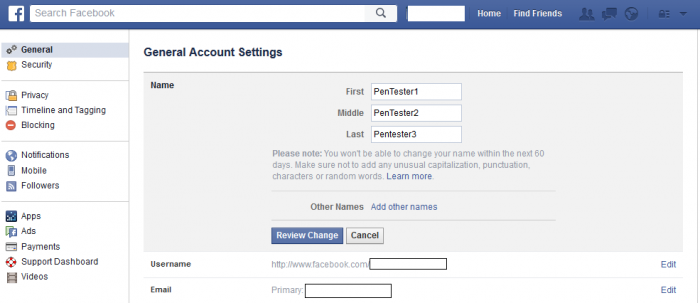
A restriction/limitation bypass web vulnerability has been discovered in the official Facebook Mobile web-application framework. Facebook limits a name change for 60 days before a new name is applied. The advisory explains how i was able to bypass the restriction to change my `Alternative name` using parameter session tampering.
First the attacker uses a restricted account (60 day) and review the changes by using a session tamper. By a permanent exchange of the name values the service updates the name value through the mobile service without usage of the secure restriction mechanism. Remote attackers are able to bypass the restriction to exploit the vulnerability. The attack vector of the issue is location on the application-side and the request method to inject is POST.
The security risk of the filter bypass vulnerability is estimated as high with a cvss (common vulnerability scoring system) count of 6.1. Exploitation of the filter mechanism vulnerability requires a low privileged web-application user account without user interaction. Successful exploitation of the bypass issue results in unauthorized account name changes through alternative name inputs.
Request Method(s):
[+] POST
Vulnerable Service(s):
[+] Facebook - Mobile Website
[+] Facebook Apps - Apple iOS & Android
Vulnerable Module(s):
[+] ./settings/account/
Vulnerable Parameter(s):
[+] name
Proof of Concept
The bypass vulnerability can be exploited by remote attackers with a restricted user account and without user interaction. For security demonstration or to reproduce the security vulnerability follow the provided information and steps below to continue.
Requirements: Attacker needs an account that changed its name and is limited for 60 (x) days before making any other changes
Manual steps to reproduce the vulnerability ...
1. Go to https://m.facebook.com/settings/account/?name&refid=70
2. Click review changes and tamper the request, change the value of
alternative name to anything
3. Continue the request and save the changed value
4. Submit request, then enter your test account password
5. Name value is changed even if time restriction was set
Note: Alternative name shall then be updated too
6. Facebook vulnerability successful exploited!
Reference(s):
https://m.facebook.com/settings/account/?name&refid=70
Time-Line
2014-12-10: Researcher Notification & Coordination (Benjamin Kunz Mejri - Evolution Security)
2014-12-11: Vendor Notification (Facebook Security Team - Bug Bounty Program)
2014-12-15: Vendor Response/Feedback (Facebook Security Team - Bug Bounty Program)
2015-01-12: Bug Bounty Reward (Facebook Developer Team)
2015-01-14: Public Disclosure (Vulnerability Laboratory)
The facebook bug bounty program payed a commercial reward to the researcher for reporting a valid security vulnerability.
Advisory: http://www.vulnerability-lab.com/get_content.php?id=1381



Add new comment