Stack Buffer Overflow Zero Day Vulnerability uncovered in Microsoft Skype v7.2, v7.35 & v7.36
Stack Buffer Overflow Vulnerability in Skype v7.2, v7.35 & v7.36
Security researchers of the vulnerability laboratory core research team uncovered a critical vulnerability in skype v7.2, v7.35 & v7.36 for microsoft windows. The vulnerability was discovered during a team conference in skype, when a crash occured during an interaction by the usual suspect Benjamin Kunz Mejri. Benjamin is well known for discovering vulnerabilities in skype software. In the last years, his researches on the software mainly stucked and no new public vulnerabilities were uncovered until 2014. The new detected vulnerability has indeed a critical impact to local and remote skype users and is explained as followed.
The skype software is using a dll in case of a copy request on the local systen. We place a picture in our clipboard (we take a screenshot in this example), this needs to be copied from a remote desktop system. This can be pasted into the local skype message box, by the paste function. Then the picture is taken from the clipboard (which is the rdp remote clipboard content) and successfully copies it into the message box.
The security vulnerability is located in the `clipboard format` function of the skype software. Attackers are able to use a remote computer system with shared clipboard to the cache to provoke a stack buffer overflow on transmit to skype. The issue affects the `MSFTEDIT.DLL` dynamic link library of the windows8 (x86) operating system. The limitation of the transmitted size and count for images via print of the remote session clipboard has not secure limitation or restriction. Attackers are able to crash the software with one request to overwrite the eip register of the active software process. Thus allows local or remote attackers to execute own codes on the affected and connected computer systems via skype software.
The attacker opens a local computer system connection and establishes a RDP connection to another system. First the attacker sets the local cache of the rdp to active to use the shared clipboard with cache. This is possible by the basic rdp settings in the `Local Devices & Resources` the clipboard to active. Then the attacker moves with a click into the rdp session window and pushes print. A screenshot is made of the remote session, that is loaded to the local system cache of the first computer system that the attacker uses. Then the attacker moves back to the local system into the conversation of skype and copypastes via strg +v the screenshot of the clipboard (print) to the message body. A clipboard error occurs because of the unknown format size and the software crashs with several uncaught access violations or unfiltered exceptions for both parties. The software is not terminated and allows to read every dll error by line with offset.
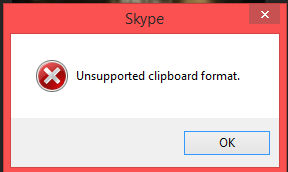
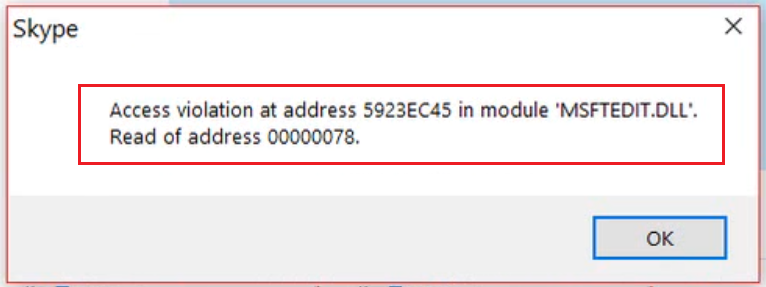
The error and critical crashs are captured by the software internal dev log called gilasterr.log file. The gilasterr.log file captures internal information of the software in case of critical errors for the skype developer teams. During the exploitation process the gilasterr.log file captured the loop crashs and overwrite of the eip register as reference. The active offsets allowed us to define a new address to compromise the targeted local or remote computer system.
The successful attack scenario is not limited to manual exploitation only. Attackers can locally prepare the cache and clipboard of a computersystem to exploit the connected remote party computer system using skype.
--- Debug Logs (EIP Overwrite) (WinDBG on Windows XP, Windows 7 & Windows 8) ---
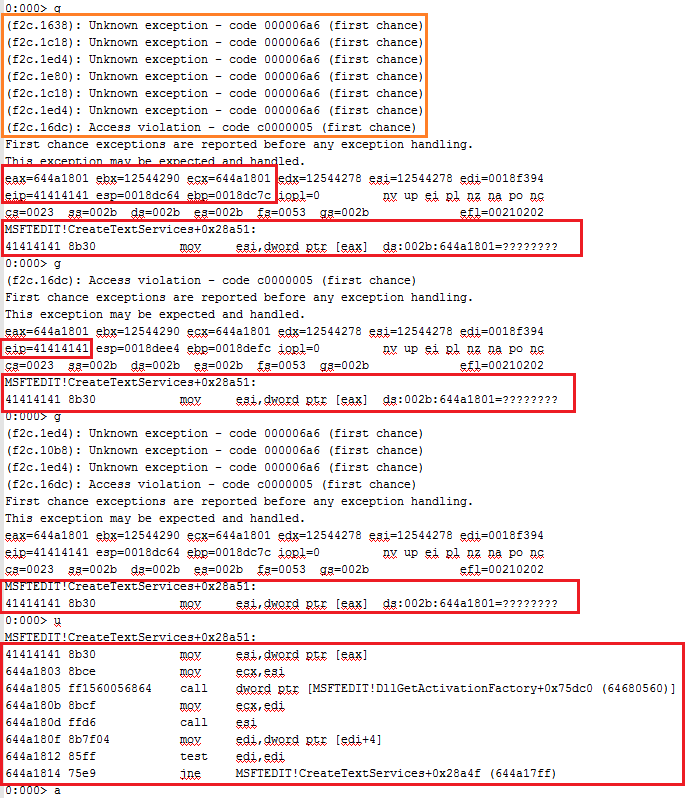
0:000> g
(f2c.1638): Unknown exception - code 000006a6 (first chance)
(f2c.1c18): Unknown exception - code 000006a6 (first chance)
(f2c.1ed4): Unknown exception - code 000006a6 (first chance)
(f2c.1e80): Unknown exception - code 000006a6 (first chance)
(f2c.1c18): Unknown exception - code 000006a6 (first chance)
(f2c.1ed4): Unknown exception - code 000006a6 (first chance)
(f2c.16dc): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=644a1801 ebx=12544290 ecx=644a1801 edx=12544278 esi=12544278 edi=0018f394
eip=00410041 esp=0018dc64 ebp=0018dc7c iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00210202
MSFTEDIT!CreateTextServices+0x28a51:
00410041 8b30 mov esi,dword ptr [eax] ds:002b:644a1801=????????
0:000> g
(f2c.16dc): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=644a1801 ebx=12544290 ecx=644a1801 edx=12544278 esi=12544278 edi=0018f394
eip=00410041 esp=0018dee4 ebp=0018defc iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00210202
MSFTEDIT!CreateTextServices+0x28a51:
00410041 8b30 mov esi,dword ptr [eax] ds:002b:644a1801=????????
0:000> g
(f2c.1ed4): Unknown exception - code 000006a6 (first chance)
(f2c.10b8): Unknown exception - code 000006a6 (first chance)
(f2c.1ed4): Unknown exception - code 000006a6 (first chance)
(f2c.16dc): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=644a1801 ebx=12544290 ecx=644a1801 edx=12544278 esi=12544278 edi=0018f394
eip=00410041 esp=0018dc64 ebp=0018dc7c iopl=0 nv up ei pl nz na po nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00210202
MSFTEDIT!CreateTextServices+0x28a51:
00410041 8b30 mov esi,dword ptr [eax] ds:002b:644a1801=????????
0:000> u
MSFTEDIT!CreateTextServices+0x28a51:
00410041 8b30 mov esi,dword ptr [eax]
644a1803 8bce mov ecx,esi
644a1805 ff1560056864 call dword ptr [MSFTEDIT!DllGetActivationFactory+0x75dc0 (64680560)]
644a180b 8bcf mov ecx,edi
644a180d ffd6 call esi
644a180f 8b7f04 mov edi,dword ptr [edi+4]
644a1812 85ff test edi,edi
644a1814 75e9 jne MSFTEDIT!CreateTextServices+0x28a4f (644a17ff)
0:000> a
The "gilasterr.log" is a file that can be used by the developers of skype to identify software issues or vulnerabilities in the moment an issue occurs. The log takes the registers of the process and dumps the raw line into the file in case of an uncaught exception. Developers are able to interpret the error logs with the dump files and event logs to reproduce or to understand an issue. The log does not integrate any comments outside the basic registers.
Exce) esi=591429f8 edi=1aa5c3d0 ebp=19da88 esp=19d8a0 eip=00410041 eax=1aa5c3b8 ebx=79 ecx=78 edx=19daac f=10206
Exce) esi=591429f8 edi=1aa5c3d0 ebp=19da88 esp=19d8a0 eip=41414141 eax=1aa5c3b8 ebx=80 ecx=78 edx=19daac f=10206
The now following event low shows that the error the overwrite has been occured. The BEX exception shows there is an overflow, the offset is visible overwriten and the problematic is followed by another critical access violiations with uncaught exceptions.
--- Error Event Log Report (Final Stack Buffer Overflow) ---
EventType=BEX
UploadTime=131396017045953454
ReportIdentifier=762751ed-3bee-11e7-8ab7-eaa72e69e267
IntegratorReportIdentifier=6d4bfe78-0289-4d95-9560-e84dc4fda8c5
WOW64=1
NsAppName=Skype.exe
AppSessionGuid=000003b8-0001-0094-b635-203efacfd201
TargetAppId=W:00065514750fd91b9e1d7f9edd239a15171d00000904!000014ddb0fbc81557d09d66c4c18c51c71ff4218649!Skype.exe
TargetAppVer=2016//08//17:21:47:12!1c3188d!Skype.exe
BootId=4294967295
Response.BucketId=1a45da49e92037f743652f4734fcab85
Response.BucketTable=5
Response.LegacyBucketId=50
Response.type=4
Sig[0].Name=Anwendungsname
Sig[0].Value=Skype.exe
Sig[1].Name=Anwendungsversion
Sig[1].Value=7.3.6
Sig[2].Name=Anwendungszeitstempel
Sig[2].Value=57b4db60
Sig[3].Name=Fehlermodulname
Sig[3].Value=StackHash_a309
Sig[4].Name=Fehlermodulversion
Sig[4].Value=0.0.0.0
Sig[5].Name=Fehlermodulzeitstempel
Sig[5].Value=00410041
Sig[6].Name=Ausnahmeoffset
Sig[6].Value=PCH_F2_FROM_ntdll+0x0006EB8C
Sig[7].Name=Ausnahmecode
Sig[7].Value=c0000005
Sig[8].Name=Ausnahmedaten
... ...
EventType=APPCRASH
ReportIdentifier=ae0d806d-3bee-11e7-8ab7-eaa72e69e267
IntegratorReportIdentifier=cb6001f2-8e24-428e-9681-798213e07167
WOW64=1
NsAppName=Skype.exe
AppSessionGuid=000003b8-0001-0094-b635-203efacfd201
TargetAppId=W:00065514750fd91b9e1d7f9edd239a15171d00000904!000014ddb0fbc81557d09d66c4c18c51c71ff4218649!Skype.exe
TargetAppVer=2016//08//17:21:47:12!1c3188d!Skype.exe
BootId=4294967295
Response.BucketId=ec621c6ccac633fce5d1e2a3190c48cb
Response.BucketTable=1
Response.LegacyBucketId=108928879505
Response.type=4
Sig[0].Name=Anwendungsname
Sig[0].Value=Skype.exe
Sig[2].Name=Anwendungszeitstempel
Sig[2].Value=57b4db60
Sig[3].Name=Fehlermodulname
Sig[3].Value=StackHash_c2f6
Sig[4].Name=Fehlermodulversion
Sig[4].Value=10.0.14393.479
Sig[5].Name=Fehlermodulzeitstempel
Sig[5].Value=58256ca0
Sig[6].Name=Ausnahmecode
Sig[6].Value=c0000374
... ...
AppCrash_Skype.exe_d0af9530b99d8758e9db661d96b23628d951d0de_1523a347_02d1c738
AppCrash_Skype.exe_eaf5689fdd6d20b6c7ce5c3281fbab78bcbc4c7_1523a347_1416ac1a
To classify the vulnerability has been reproduced for microsoft several times in different videos. One of the reproduce videos has been shared by the german researcher.
In a software update of the 7.35 to 7.36 version of skype a limitation has been implemented for the clipboard function. Due to the implementation a misconfiguration was included by the developers. The cut function allows to paste the image in raw format back to the message box. After the limitation was implemented for the pasted image counts and for the byte size of the clipboard, the attacker is still able to exploit the issue. Therefore an attacker uses the developer flaw that should fix the new zero-day vulnerability. The attacker copies the content via remote session of the clipboard via cache, then he uses the cut ability of skype with the context menu and repaste the input again. After that the images are getting transfered in raw format as text value of the skype code [image] by repasting them to the message box query, the vulnerability can be triggered again and the limiation of size and count is bypassed.
The vulnerability was reported to the microsoft security response center 16th may 2017. The security vulnerability was resolved by a stable patch during an update to version 7.37 of the skype software. The cvss of the vulnerability is estimated as high with final count of 7.2.
Advisory: https://www.vulnerability-lab.com/get_content.php?id=2071
References:
Note: The issue was identified in may 2017. The article was written in june 2017 and the disclosure was 26th july 2017.



Comments
didnt notice the gilaster log
mister, you are some special
first public stack overflow
Add new comment